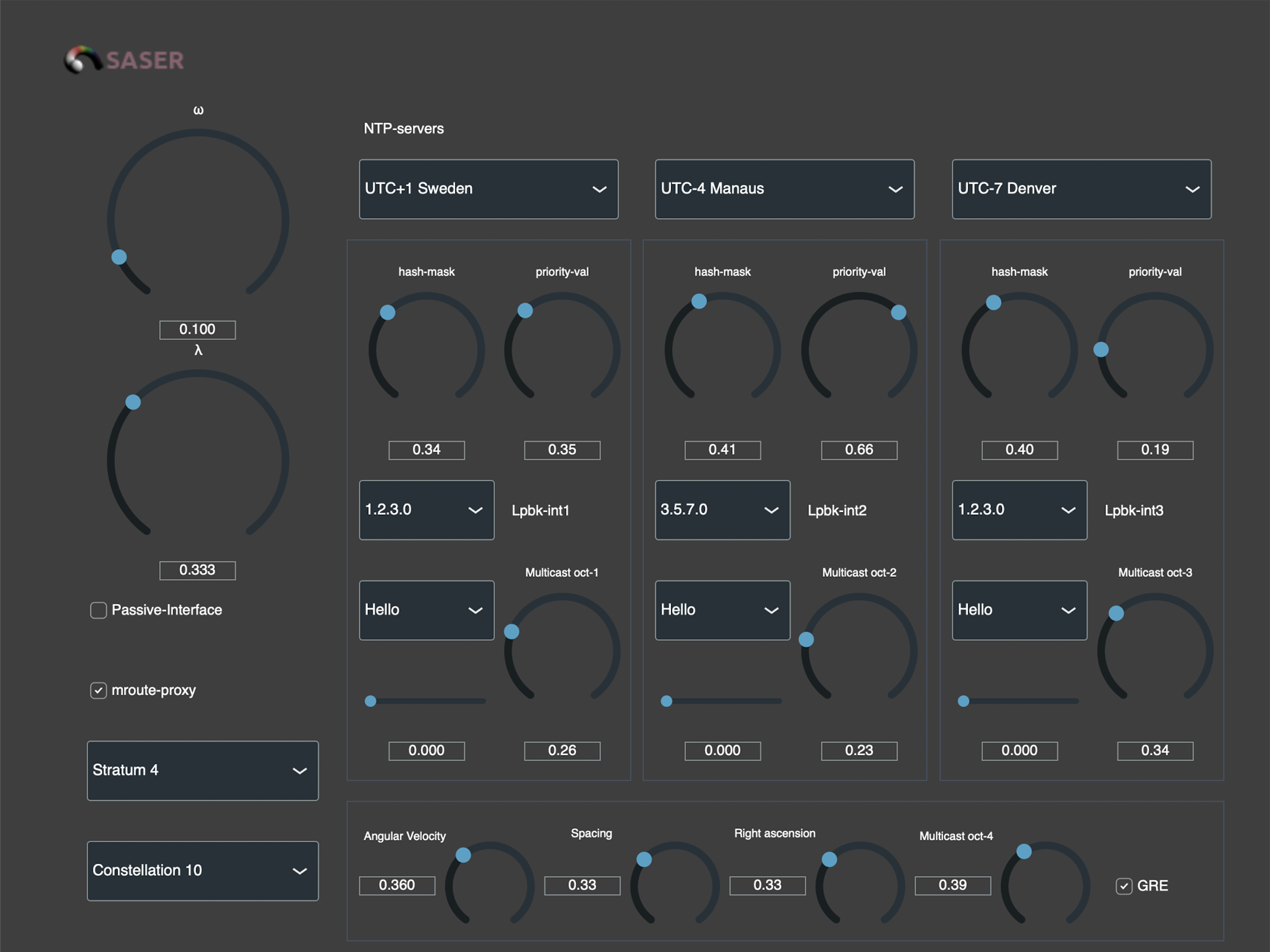
Notification to users of software products of Compositor Software. Dear users, as you already know, the final Compositor Software application called SASER 2.0 has been on sale for a year. However, this is not the second version of this program. History goes far back in time. And it all starts with a geography lesson in 1996 by Ruslan Yusipov, a…