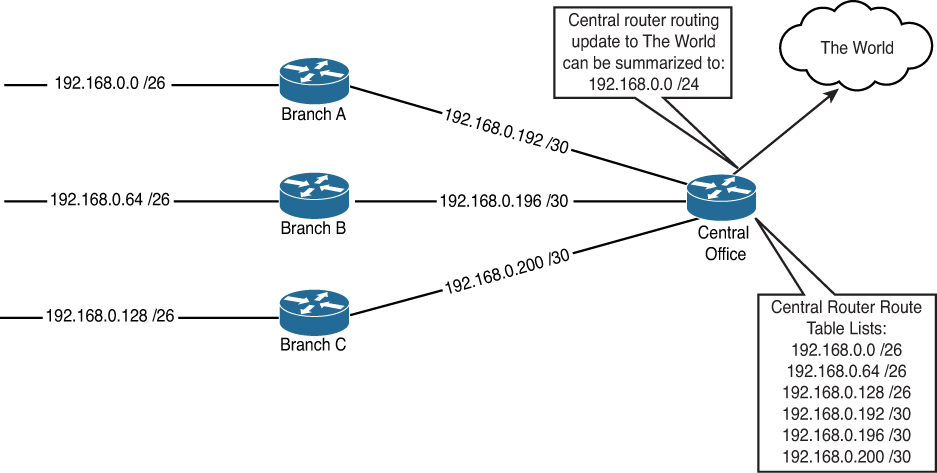
Automatic summary strategy Merging peers in response to a summary happens with extended denial of peers according to the ACL. When mirroring with multiple peers, the Compositor neurological chipset combines peers in milliseconds. If a peer is known as a false host in the ACL database, it is rejected. The local image then works to restore the local peer to…