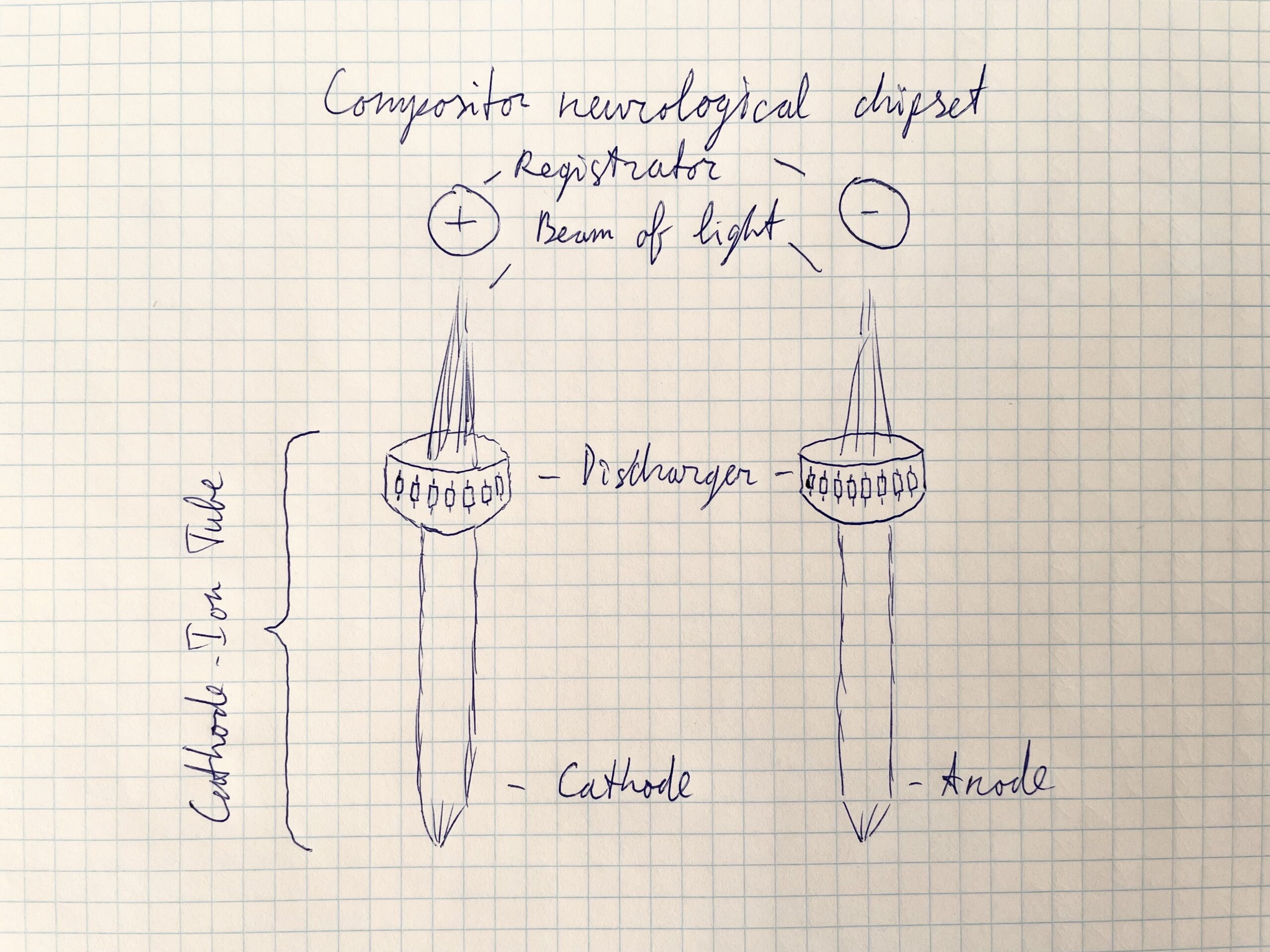
Neurological chipset from Ruslan PC Compositor Software presents the Ruslan-PC.com website dedicated to a new product in the computer services market: a neurological chipset. This site provides information about the product and the stages of its development. A neurological chipset is a set of two applications for the Android platform that interact with each other and create a communication environment…